The way you organize, monitor, manage and report the user access to these various resources while meeting audit and compliance requirements is what is Identity Governance and Administration (IGA) all about.

Necessary but not a necessary evil
IGA technology is key to manage identity and access across your organization. It will enforce that the right people get the right access to the right resources at the right time for the right reasons.
There are more advantages to IGA technology than just the ease of identity access management.
- It will ease compliancy, using central reporting of access across your organization
- It will also enable you to enforce 'least privilege' and 'need to know' principles by only granting the authorizations that are required and approved.
- By automating processes as much as possible, less staff is needed to execute authorization requests, reset passwords and deliver reports.
- Due to the link with “authoritative” sources (for example an HR system), the access to resources is in sync with employees that are active within your organization.
- It ensures that employees are onboarded faster, have the right access in their new role and are enabled from day 1.
What are you risking?
An IGA system has tools which provide an organization insight into IT risks.
- Certification is a process in which a manager or application owner revises, revokes or confirms the authorizations of employees at regular intervals
- Classification of resources provides insight into which risk is associated with a resource, and which employees have privileged access to critical resources.
- Segregation of Duty identifies combinations of authorizations that may pose risks. For example an employee who can approve his own expense notes
These tools are needed to shift from functionality and efficiency (managing access) to mitigating corporate risk. This will increase the awareness in the organization related to identity and access management.
Rome wasn’t built in a day
Implementing IGA is a process where the organization will mature together with a growing awareness of identities and access. This is not a one-off project, it’s rather an evolution. An organization must go through different stages of the IGA best practice approach to have fully implemented functionalities of IGA.
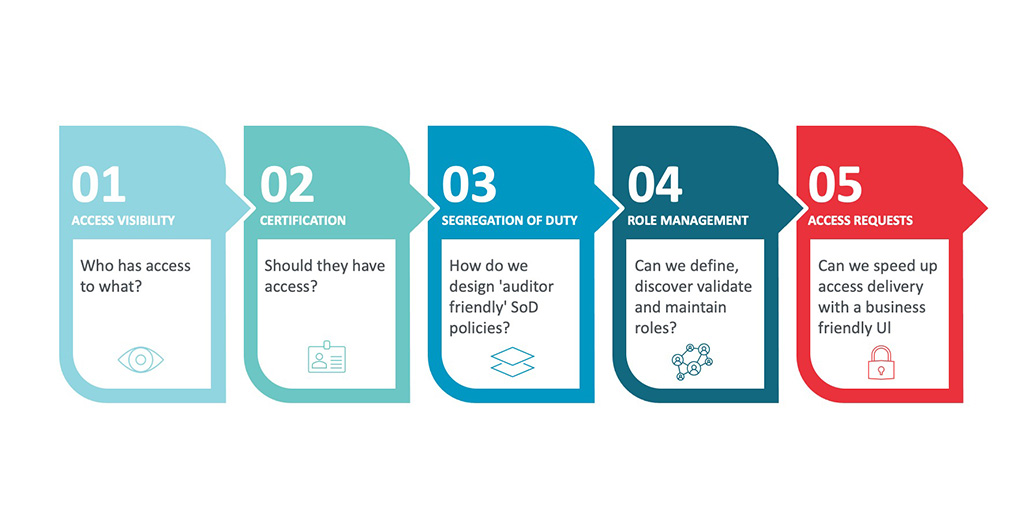
The right access to the right resource
As your organization evolves, you need to keep up with the access to all resources. IGA helps you to enforce that the right people get the right access to the right resources at the right time for the right reasons. The system will provide the organization with insights into IT risks. Implementing IGA is not one-off project, rather an evolution. IGA is fundamental for compliancy, avoiding labor intensive tasks and reducing business risks and helps you to get in control of IAM.

