For that reason, it’s best to first think about what keeps an organisation running, and to build the security strategy around that. You then make the investments which will protect your organisation’s most important assets. These are usually the ones that will cost you the most if there is a breach. Is it your database? Your webstore? Your factory? It’s different for each organisation, but we do notice four trends.
Trend 1: EDR against advanced cyberattacks
Cyberattacks are become increasingly advanced. It is taking much longer for a breach to be detected. In this challenging context, your main priority is that your business keeps running. You therefore need to prevent your devices being entered by cybercriminals or infected with malware.
Classic proxies or firewalls, for example, form a first line of defence. But if you restrict your protection to these solutions, it will give you a false sense of security. After all, such software will stop a lot of attacks, but the protection is never 100%. These solutions attempt to prevent breaches, but they lack the functionality to detect.
You have to assume that your IT systems will be breached at some time. And what do you do then? You need a second line of defence to detect when an attack breaks through the first line. That is Endpoint Detection & Response (EDR).
For EDR, you install an agent on each device (computer, telephone, tablet) to detect breaches on that device. This process happens in an intelligent way. The agent monitors the behaviours of the user and the programs on the device. If anything abnormal happens, the agent sounds the alarm.
As soon as malware or a cybercriminal breaks through the first line of defence, the EDR’s work begins. Because it continuously monitors all actions on the device, there are various moments during the breach when EDR can sound the alarm. For example, at the moment when the malware is first executed, the moment when the malware tries to save itself to the device, or the moment when it tries to acquire more rights.
EDR doesn’t only use learning processes (machine learning) to recognise suspicious behaviour. The technology can also fall back on cyber threat intelligence: all kinds of external information about attacks in other organisations. In that way, an agent in your device can sound the alarm if it detects behaviour that has already been identified as dangerous somewhere else.

Trend 2: NDR to regain control
Due to COVID-19, working at home has drastically increased, and with it the amount of network traffic. And we are making increasing use of IoT devices or SaaS applications, over which we have less control. You cannot install an EDR agent on these.
For this, Network Detection & Response (NDR) offers an additional layer of protection, on top of a firewall for example. With NDR, you control what is communicated between devices rather than what happens on those devices. NDR analyses the network traffic for suspicious patterns. Because the control is exercised passively, the impact of this protection layer on the business is also limited.
Even if the network traffic is encrypted, such an analysis provides useful information. For example, a sudden increase in encrypted traffic to an unknown server can indicate a malware infection.
If NDR then detects suspicious network traffic, it can instruct a firewall to block communication with the device or server.
Trend 3: Brand intelligence for insight into the cyber underworld
For good protection, it’s no longer enough to look at what is happening in your own infrastructure. After all, the cyber underworld is expanding all the time. You don’t have the time to monitor all that yourself. If, for example, you have already had an unnoticed cyber breach, there is a likelihood that the stolen data is being offered on the dark web. Can you monitor that?
Also, you would want to know as quickly as possible if someone registered a domain name that closely resembled that of your organisation. After all, there is a good chance that the domain name will be used in a phishing campaign to trick your users or customers.
The same applies if a false mobile app from your organisation appears in the Apple or Google app stores. The faster you detect this, the faster you can prevent an attack using it.
We call this analysis of what is happening outside our own infrastructure brand intelligence. It is an essential supplement to EDR and NDR for the protection of your organisation.
Trend 4: XDR for a holistic and customised approach to your organisation’s security
EDR, NDR and brand intelligence each resolve individual problems, but security is a multi-dimensional problem. You can never deal with that fully using partial solutions, each of which operates in isolation. You need a holistic approach to security.
A solution that handles security as a whole is eXtended Detection and Response (XDR). As well as EDR, NDR and brand intelligence, XDR uses SIEM and SOAR:
- SIEM (Security Information and Event Management) collects logs from all kinds of sources (servers, applications, network devices etc.), correlates that data, and delivers realtime analysis and notifications of suspicious events.
- SOAR (Security Orchestration, Automation and Response) is a system that responds automatically to incidents identified by EDR, NDR, brand intelligence and SIEM. In this way, it flexibly connects the various partial solutions to create a customised solution for your organisation’s specific problems. If, for example, you get brand intelligence about a phishing site, you can automatically block all communication to that website.
With XDR, the task of the SOC (Security Operations Center) also changes. A modern SOC team consists not only of analysts who monitor threats to your IT infrastructure, but also of SOC engineers who automate your security tasks in SOAR playbooks.
Conclusion
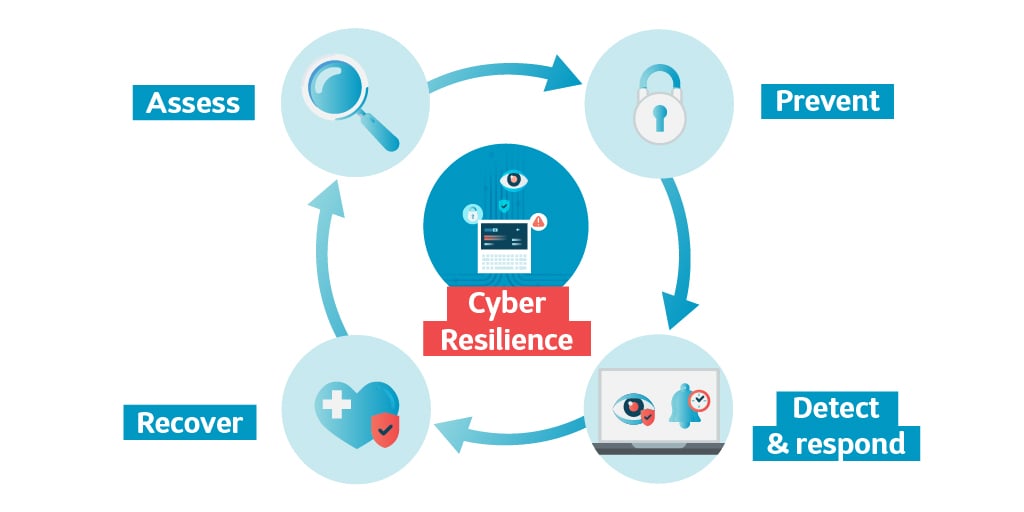
Your organisation will never be 100% protected, and your budgets are not bottomless. However, with a continuous process for improvement and a focus on Return On Security Investment, your organisation will become a bit more secure with each day. We call this cyber resilience. When you are cyber resilient, you give proportionate attention to the four components of the continuous security process:
- Assess: Understanding your risks.
- Prevent: Preventing attacks insofar as possible.
- Detect & respond: Detecting when, despite all efforts, there is a breach, and respond to it.
- Recover: Recovering quickly and efficiently from a breach.
In this way, you can protect your organisation against the latest trends in cybercrime.

